Software to elevate your security program
Imagine modern security software, purpose-built to manage threats, mitigate risks, and make businesses stronger. That’s Connected Intelligence from Ontic.

Our Products
It’s time to modernize your security program
Security is a strategic imperative for business success. Take your security team beyond reactive tactics with software that lets them get proactive — so they prevent incidents before they develop.
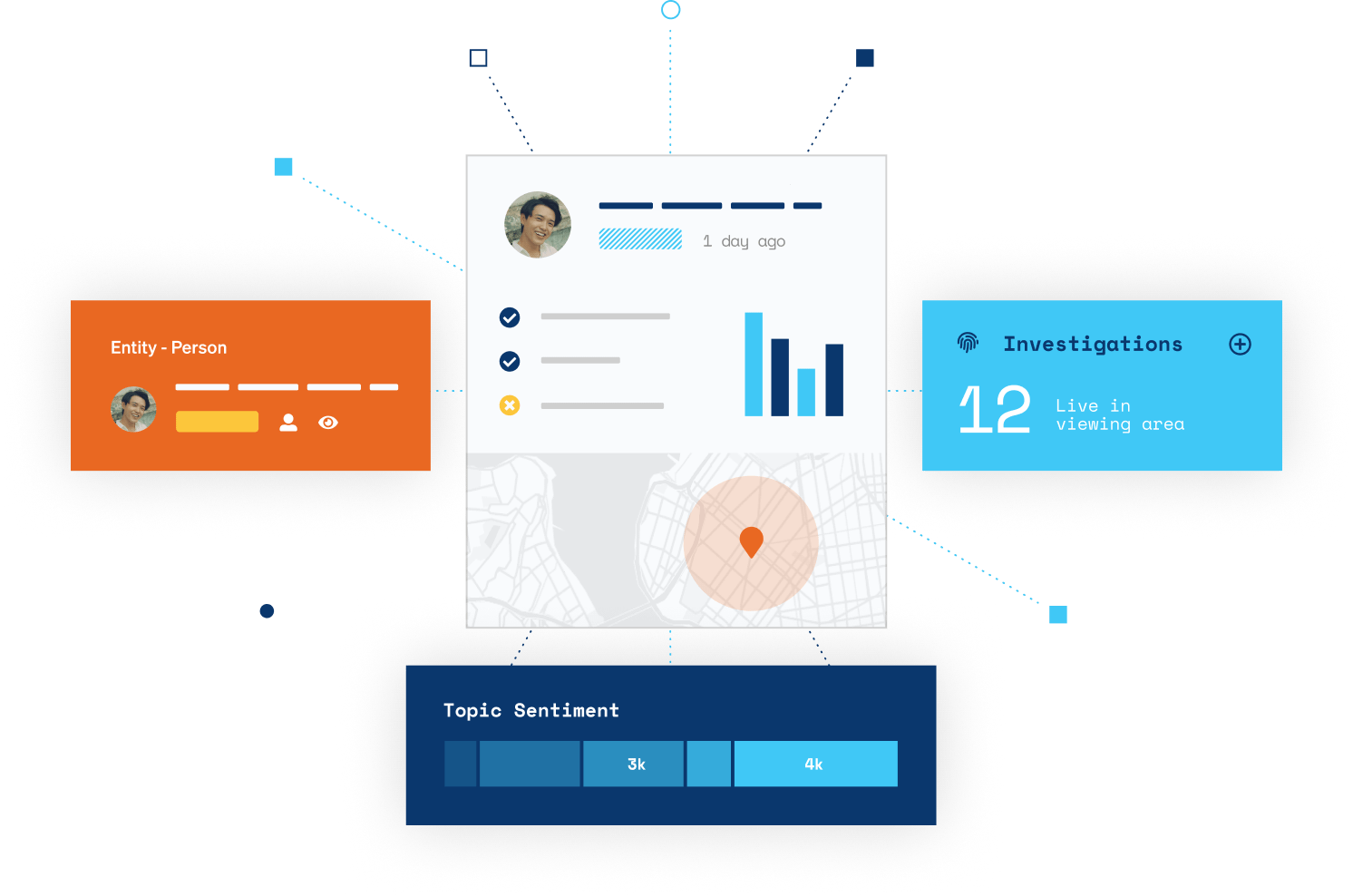
Incidents, Investigations,
and Case Management
Centralize and streamline end-to-end case management with dynamic collaboration. Manage incident logging, investigative research, reporting, and case tracking — all in one place.
Integrated Research
Broaden intelligence and deepen investigations with insights combining real-time and historical data. Optimize threat detection with identity, criminal activity, civil litigation, adverse media, and global intelligence coverage.
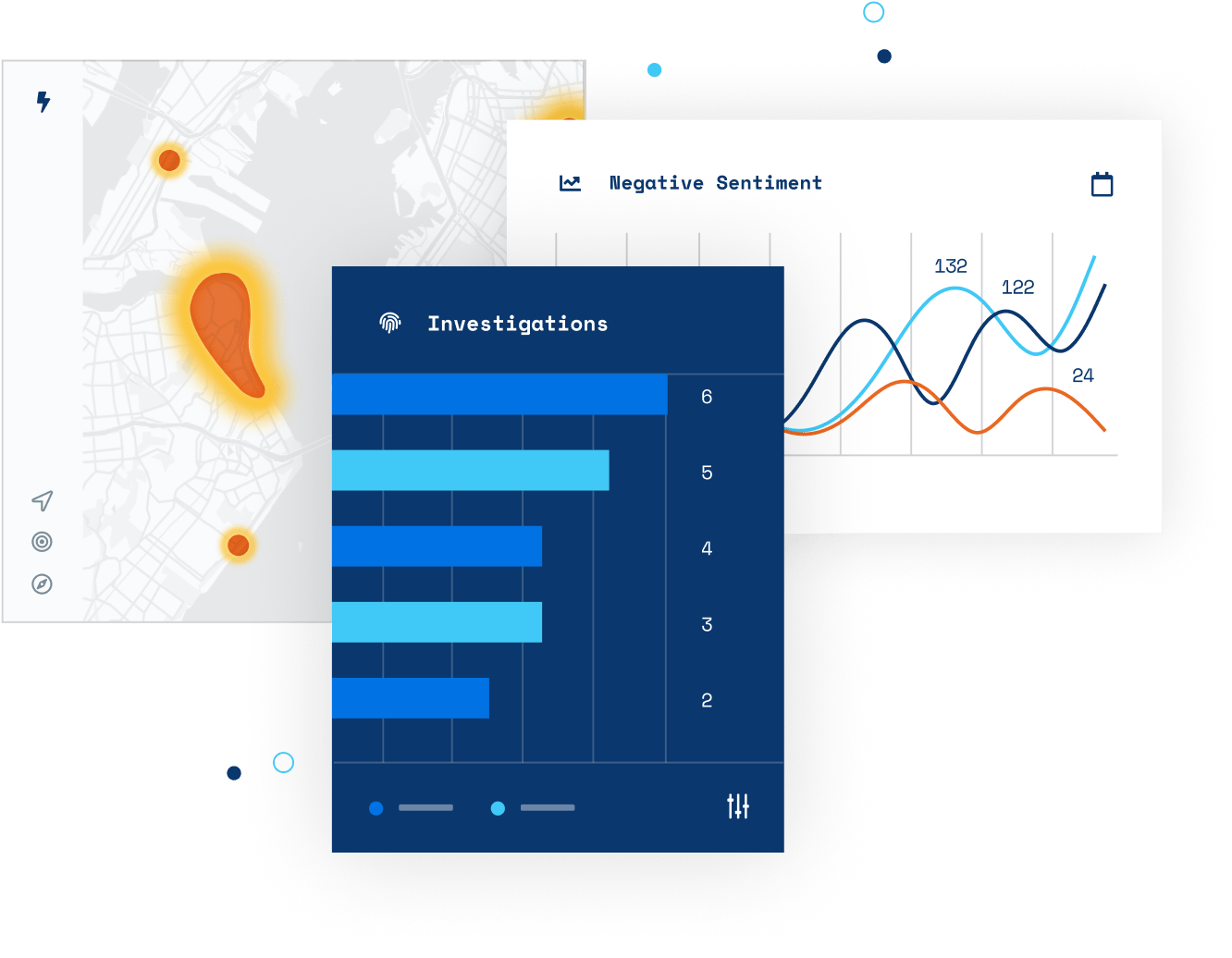
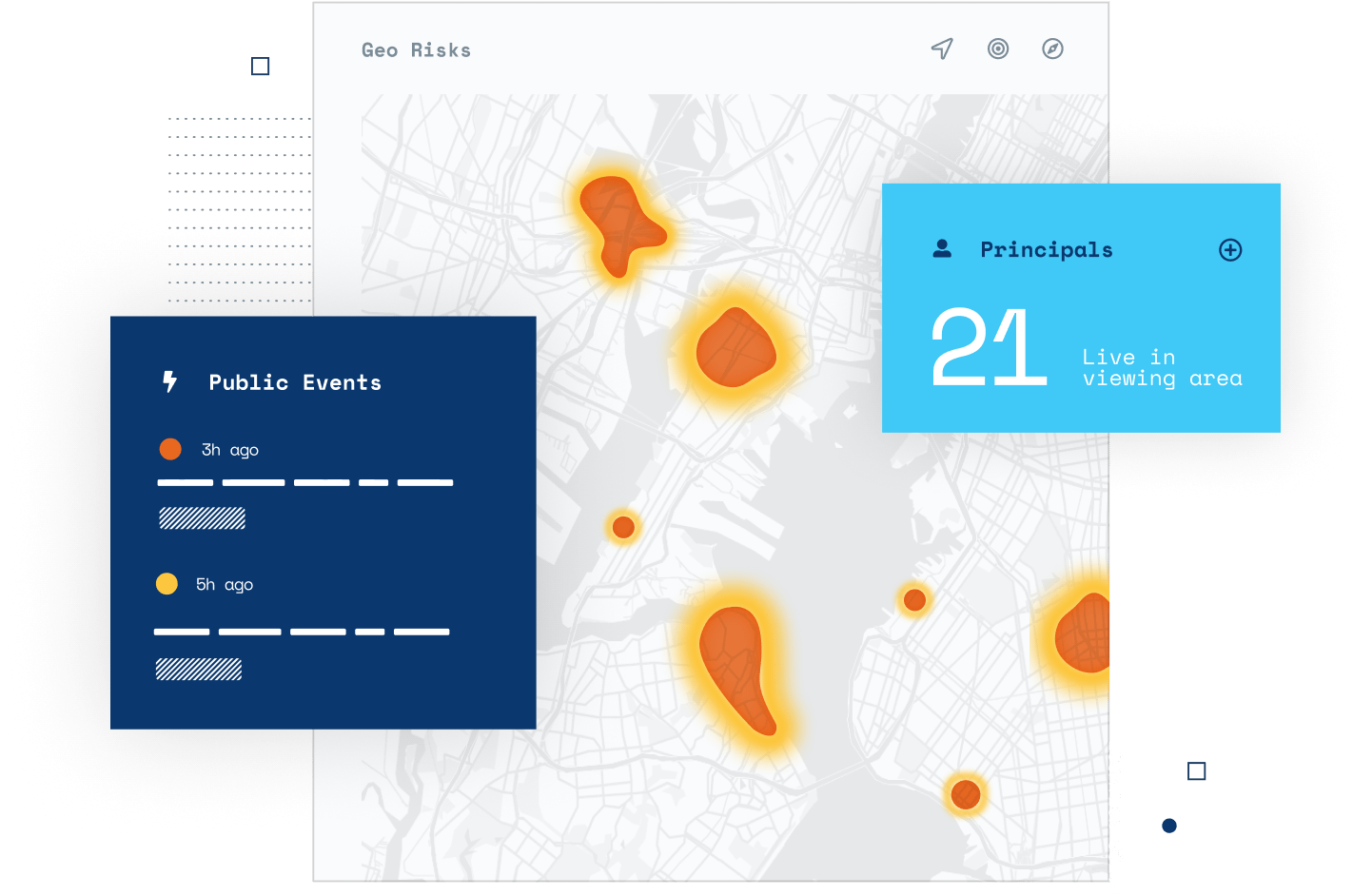
Real-Time Threat Detection
Discern critical signals through the noise to gain more accurate situational awareness. Get actionable insights with automatic analysis of weather, social media trends, geo risks, and more — so you can respond proactively.
Threat, Vulnerability, and Risk Assessments
Take action before risks escalate with a tailored program for assessing threats and vulnerabilities. A guided plan for risk management with unified workflows empowers teams to keep business moving while mitigating risks.
The Ontic Platform
Connected Intelligence is the answer
Say goodbye to separate security systems and silos that hide threats in plain sight. The Ontic Platform connects your people with critical data to enable more confident decision-making. With Ontic, people stay safer and businesses grow stronger.

Ontic Resources
Connected Corporate Security Report
Download our new report written in partnership with The Clarity Factory to learn how corporate security teams are well-positioned to be connectors across the business and help eliminate blindspots.
Our Clients
We’ve earned the trust of the world’s top brands
How do we do it? Ontic knows the real-world challenges today’s corporate security teams face. When we deliver Connected Intelligence, we empower security professionals to grow stronger businesses and build a safer world.

“It’s everything that we used to do but now we can do it quicker, we can do it with more accuracy and we can involve more data that we didn’t previously have.”
We do more than build
award-winning software
At Ontic, we’re transforming the practice of corporate security. We do it with four seamless products powered by the Ontic Platform. We also do it by bringing leading security thinkers together and sharing trusted resources created for security teams everywhere.
Ontic Resources
Expert how-tos, essential checklists, and resources to help you get security done.
The Ontic Center for Connected Intelligence
Learn from the security industry’s top thinkers and change-makers.